AZ-305 - AAD and access
Azure Active Directory
AD FS
AD FS is a feature within AD Connect that allows users to authenticate to the cloud using on-premises credentials (passwords).
- Establishes trust between different domains - on-premise and Azure.
- Allows users to login to Azure with on-premise password.
- Requires AD Connect to be installed.
- A forest is a group of one or more domains in ADDS.
- Trust is when one domain allows another to access its resources.
- Combine the two, and what you get is forest trust.
- Trust relationships can be:
- One-way - Domain A can trust Domain B, but not the other way around.
- Two-way - Domain A trusts Domain B, vice versa.
- Transitive - Domain A trust Domain B. Domain B trust Domain C. Therefore Domain A trusts Domain C.
- Non-transitive - self-explanatory.
AD DS

Baseline architecture for AD DS in a VNet
- Allows you to run legacy apps that can't use modern authn methods. Use Azure AD DS if there are compatibility issues for authn.
-
Fully managed domain controller that offers:
- Domain join
- Group policy
- LDAP
- Kerberos / NTLM authn
- Not to be confused with on-premise AD DS.
- Azure AD DS replicates identity information from the Azure AD (in cloud) or from on-premise AD DS (via AD Connect).
- Deploy AD DS in an Azure virtual network
AD App Proxy
AD Application Proxy allows you to auth from AAD to an on-premise application. View
- App Proxy service runs in the cloud as part of the AAD. Provides a token to be passed to the App Proxy Connector.
- App Proxy Connector is an agent that runs in a Windows server on-premise. It is stateless and pulls info from the cloud.
Access Management
AD Connect allows you to sync your on-premise AD with the cloud. By default, password hash are also synced to the cloud, but can be selectively excluded.
Identities on-premise will be synced to the cloud. But identities on the cloud remain unique. Check the identity issuer in the AAD to see which directory the identity belongs to.
Azure Managed Identity are for applications to obtain Azure AD tokens to authorize access to resources. Developers do not need to manage credentials for apps.
Azure Identity Protection is an AD tool to:
- Automate detection and remediation of identity-based risks.
- Investigate risks.
- Export risk data to SIEM (security information and event management)
Not to be confused with Azure Information Protection (AIP) which labels, classifies and protects sensitive information in documents and files.
AAD and APIM
You can combine both resources to provide app authorization to backend APIs.
- Register the backend app in AAD.
- Register the frontend app in AAD.
- Grant permission for the frontend to call the backend in AAD.
- Configure the Dev Console to call the API using OAuth2.0 in APIM.
- Add validate-jwt policy to the OAuth token for every call in APIM.
Privileged Identity Management
Azure AD PIM is used to manage users' privileged access to Azure, often by security ops.
- Manage access by reviewing, renewing, or extending access.
- Activate just in time access for time-bound roles.
- Discover and monitor access and receive notifications for new assignments.
AD PIM is under the Identity Governance resource in the portal.
- Requires Azure AD Premium P2 license. But Global Administrator and User Administrator roles to not require this license.
- Grants access to Azure resources. (I believe it's similar to MasterSAM).
-
3 main services:
- Access management
- Just in time access
- User access discovery and monitoring
Identity Governance
- Access package is a bundle of resources that users are entitled to access. Can be used to manage access to project-specific resources. It's part of the wider entitlement management concept in Identity Governance.
- Allows you to setup resources and policies once, and administers access for the package's life cycle. You need to create a catalog before creating an access package.
- Catalog is a set of resources that can be granted in an access package.
AAD hybrid solutions
There are three ways to deploy hybrid (on-prem and cloud) authentication with AAD.
Password hash sync (PHS) is deployed together with AAD Connect to extract password hash to the cloud and synced every 2 minutes.
AAD Pass-through Authentication (PTA) allows users from the cloud to authenticate via on-prem AD. Requires an agent to be installed and running on-premises.
Federation with AD FS (AD FS) also incurs overhead for running on-prem AD FS servers.
Of the three solutions, PHS is recommended for HA because PTA and AD FS requires the on-prem AD to be available for auth. However, corporate compliance must allow users' password hashes to be stored in the cloud.
Summary of different services in Azure AD
- Privileged Identity Management mainly allows you to manage just-in-time access.
- Identity Governance mainly allows you to perform access reviews.
- Identity Protection is more concerned about detecting attacks on the AD.
Other AD features
-
Smart lockout
- Locks sign-in attempts after 10 failed tries for 1 minute.
- Cooldown duration increases for subsequent failures.
- Feature is always on. Available in at least Azure AD Premium P1 license.
- Doesn't guarantee genuine users will not be locked out.
- Protects againsts password brute force.
- Secure backend web API with Azure AD

- Say you want to authenticate web applications to a backend web API.
- You need to register the web API with AAD.
- Web application will request for token from AAD.
- Web application will use the token to call web API.
- Authentication happens at the web API.
Managed identities
System-assigned identities will be deleted when the resource it's attached to is deleted.
User-assigned identities are independent of the resource's lifecycle.
Not to be confused as a managed identity:
External identities allows users to use social identity like Google and Facebook or SAML/WS-Fed IdP to be authenticated.
Action groups
Action groups are collections of notifications configured to notify users of alerts.
Can be created by navigating Monitoring > Alerts > Action Group from any resource. (doesn't appear in seach bar). Some services allow you to send notifications directly to an email without having action groups.
Service principal object
There are 3 types of service principals:
-
Application
- Represents an app in a single directory. If you register the same app in two directories, the app would have two identities.
- This service principal defines what the app can access in its tenant.
-
Managed identity
- Eliminates the need for developers to manage credentials.
- Managed through AAD authn.
-
Legacy
- Not associated with registered apps.
- Can be used only where the tenant is created.
Conditional Access Policy
- Part of the Azure AD service. Requires Azure AD Premium P1 license.
-
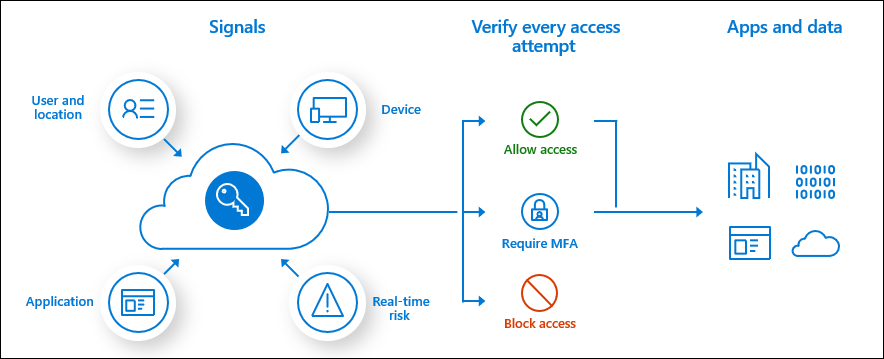
Three core concepts:
-
Signal
- User or group
- IP location
- Device
- Application
- Real-time risk calculation (sign in behaviour)
- Microsoft Defender for Cloud Apps (monitor user access and sessions)
-
Decision
- Block access
- Grant access (with conditions: MFA, compliant devices, approved client apps, app protection policy)
- Enforcement
-
Shared access signature
Delegates access to services in Storage account.
-
User delegation SAS
- Applies to Blob storage only.
- Secured with AAD and the associated permissions.
-
Service SAS
- Applies to only one Storage service - Blob, Queue, Table or Files.
-
Account SAS
- Applies to one or more storage services.
- Secured with storage account key.
-
Delegates permissions to:
- Read, Write, Delete operations that aren't permitted with service SAS.
- Service-level operations (Get properties or stats).
Back